The famous Charlie Miller (on Govt funding) shows how to hack a car. The brakes, the speed, fuel-gauge and everything else! You Tube video here.
Update 01-Aug-2013:
A similar hacker/researcher in UK, has been banned by the court to reveal his findings.
2013-07-28
2013-07-22
Millions of mobile sim cards vulnerable!
Mobile sim cards, which are still on the old technology, with DES encryption are all vulnerable to an attack
2013-07-21
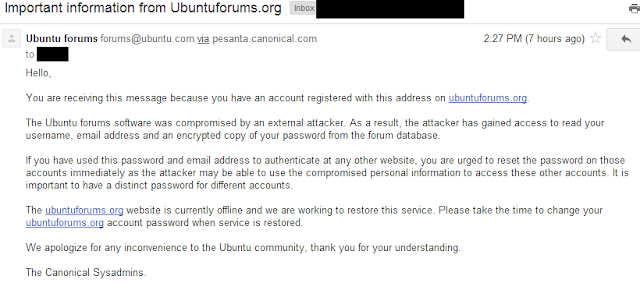
Ubuntu Forums Hacked - 2M Accounts Breached
UbuntuForums has been compromised and led to all the accounts credentials being stolen. The site (thankfully) discloses that the passwords were not stored in plain text, but doesn't mention if best-practices like salting were used. Sputn1k has claimed responsibility.
Update 24-Jul-13:
An email received from Ubuntu:
Update 24-Jul-13:
An email received from Ubuntu:
2013-07-17
Tumblr Passwords Compromised
Tublr asks users to change their passwords. Some mobile app of theirs sent passwords in clear text
2013-07-12
Security for the paranoid!
We all have 100s of accounts, with multiple passwords. So, how can we ensure user friendliness of a password manager, but from a truly [paranoid] security guy's point of view?
We are heading into a world of cloud computing where trust is going to be a huge issue. It is no longer simply a matter of trusting that the software you buy works as advertised.
India VS RIM
I thought I had blogged about the Government of India and Blackberry's RIM debate. But, I can't find it now. Basically the government is pressurizing for something that does not exist.
Update: 06-Jan-13
RIM gives in and sets up a monitoring facility for the Govt of India.
Update: 12-Jul-13:
Looks like BB/RIM finally gave in to the demands of the Indian Govt. But, earlier didn't they say they do not have access to the encryption keys, so how does this magic happen now?!
Update: 06-Jan-13
RIM gives in and sets up a monitoring facility for the Govt of India.
Update: 12-Jul-13:
Looks like BB/RIM finally gave in to the demands of the Indian Govt. But, earlier didn't they say they do not have access to the encryption keys, so how does this magic happen now?!
2013-07-09
Thousands of Club Nintendo accounts compromised
Following the footsteps of the Sony PlayStation hack, accounts of thousands of Nintendo users have been compromised.
99% of Android Devices Vulnerable
Impact: Every device sold since Android 1.6 (Donut); that is, nearly 900 million device
Update 17-Jul-13:
A second similar master-key vulnerability has been discovered.
[Quote] The vulnerability is a code signing flaw. Developer's 'sign' their apps with a cryptographic signature. That way, only the app developer is able to update or modify an existing app, because only the developer has the signature. Bluebox has discovered a way to subvert this. "This vulnerability makes it possible to change an application’s code without affecting the cryptographic signature of the applicationBlog from the Bluebox - a new player in the market
Update 17-Jul-13:
A second similar master-key vulnerability has been discovered.
2013-07-08
Data Leakage By Dumb Employees
How do you know, if your users have auto-forward feature enabled on their email systems? Risk here of course being that confidential data of the organization goes out automatically? How do you detect such offenders? It's harder than you would think it would be
2013-07-06
Carberp financial malware gets leaked online
Source code for a malware, which originally costs $5000, is up for grabs. Go ahead and tweak your own free malware!
Update 18-Aug-2013:
Here is a link to download it.
Update 18-Aug-2013:
Here is a link to download it.
A world record attempt at CTF Hacking Contest
An inspirational attempt to get 3000+ security enthusiasts together and play the Capture The Flag hacking game. If successful, they will go down in the Guinness book of world records! Do watch their youtube video
Microsoft announces a bug bounty program
Microsoft, even though late in this game, has finally announced their very own bug bounty program.
More details of how it works, pays at least $500!
More details of how it works, pays at least $500!
Pakistan Goes For Internet Censorship
Looks like Pakistan is on the same route as China, and will start censoring the internet!
Subscribe to:
Posts (Atom)