2013-12-22
Disable webcam light on Windows
There were some news in the recent past of govt and hackers (both!) hacking and using a person's own webcam to spy on him. The question was how they keep the webcam light switched off while this is done. Here's how on windows.
2013-12-16
Anonymous plays Robin Hood on Xmas!!
Kudos to them!
TeamBerserk hacktivists launch #opBerserkChristmas, a campaign to buy 'thoughtful gifts' for the unfortunate paid for with credit cards belonging to naughty government officials, politicians and corporations.
2013-12-14
2013-12-10
Rogue certs for Google domains issued!
Update 10-Dec-13:
An intermediate certificate authority (CA) registered to the French Ministry of Finance issued rogue certificates for several Google domains without authorization. Link
2013-12-08
2013-11-30
GitHub gets a brute force attack
While we aggressively rate-limit login attempts and passwords are stored properly, this incident has involved the use of nearly 40K unique IP addresses.The official post
2013-11-12
Bitcoin Banks hacked
The site claimed to be "one of the most secure web wallets on the market" and charged customers a small fee to store their coins.$ 1.3M stolen
Update 14-Nov-2013:
Bitcash.cz now hacked and 4000 coins stolen!
Update 30-Nov-2013:
A Danish exchange now goes down and lose 1295 coins!
At the same time the cost of 1 coin crosses $1200!
Update 01-Dec-2013:
Virtual Currency Explained (Like You're an Idiot)
Another very good explanation. How the protocol works.
Update 08-Dec-2013:
Another site [Sheep Marketplace] gets hacked of bitcoins. Or is this a case of the website owner stealing them?
Update 14-Feb-2014:
SilkRoad 2 hacked and robbed of $2.7M. How did the Feds find the identity of their servers - via reCaptcha!
Update 19-Feb-2014:
What's going on at Mt. Gox
Update 25-Feb-2014:
Mt Gox shuts down! Bitcoin-stealing malware hidden in Mt. Gox
History of Bitcoin
Update 08-Mar-2014:
Bitcoin creator found? Turned out to be false
Update 22-Mar-2014:
Mt Gox 'finds' $100m worth of coins?
Update 26-Apr-2014:
Physical debit cards for bitcoin
Update 01-May-2014:
MIT Students Look To Jumpstart Bitcoin Economy
Update 15-Sep-15:
Seems like Mt Gox case, isn't about hacking/malware, but about embezzlement. Former founder and CEO has been arrested in Japan.
Update 08-Dec-15:
Internet now believes that a Craig Steven Wright, from Australia, is the mastermind behind BitCoin (the Nakamoto). His house got raided, and he is under arrest now.
Update 03-May-16:
Craig comes out and admits he is Nakamoto. We also have skeptics who (very convincingly) believe this is just a lie.
Update 07-May-16:
Woh, Craig backtracks, and takes down his blog which he kept over the years. All there is now a goodbye message.
Update Feb-2017:
Zerocoin loses $585 K because of a bug in their code.
2013-11-11
Culprit of corporate wide infections
Who is the biggest culprit when it comes to corporate wide infections? It's the senior management!!
ThreatTrack found that bosses, or senior leadership, end up with malware on their PC or mobile device by:
56% clicked on a malicious link in a phishing email.
47% attached an infected device to a corporate PC.
45% let a familiy member uses a company computer.
40% surfed to a malware-infected porn site.
33% installed a malicious app.
Anonymous attacks Singapore
2013-11-10
Spike in traffic with TCP source port zero
Someone's going after TCP port 0. Some new kind of reconnaissance is in progress - heads-up!
PCI DSS gets updated
Finally an updated version for the so-called de-facto standard for the credit card industry.
The new version will go into effect on Jan. 1, but organizations will have until Dec. 31, 2014, to make the transition from PCI DSS 2.0. In addition, some of the new security requirements will have the status of best practices until June 30, 2015.
2013-10-29
Pres Obama gets pwned
URL shortening service of twitter was hijacked, to point Obama's URL's to a youtube video on Syrian terrorism. The motive:
"Obama doesn't have any ethical issues with spying on the world, so we took it upon ourselves to return the favor"
2013-10-28
2013-10-19
Shodan Search Engine
Introducing a search engine, which goes beyond Google's (only web page) searches.
2013-10-16
Lock your PC before leaving your desk!
As security professionals, it is extremely hard to educate users for basic security awareness. The simplest being, locking their PC (Windows Key + L), before leaving their desks. Here are some hilarious pranks to run on such users, to educate them (AKA teach them a lesson)!
2013-10-15
Thousands of sites hacked via vBulletin vulnerability
If you are running vBulletin check your website now! Thousands have already been hacked.
2013-10-09
AVG and WhatsApp hacked by Palestinian Hackers
It is always embarrassing when security companies get hacked! AVG joins that (not so) elite club. WhatsApp is pretty known to have security holes, so no news there.
2013-10-05
Your corporate network is already compromised
2013-10-04
Adobe Hacked!
Hackers stole (hopefully) encrypted credit card data from Adobe. The hack apparently took place around 11-Sep, but was only 'recently' discovered!
Moreover, 40 GB of source code of Adobe products have been stolen as well. Which means we can now expect even more sophisticated malware
Update 29-Oct-2013:
3 million encrypted customer credit card records stolen. At least 38 Million users impacted. More details
Moreover, 40 GB of source code of Adobe products have been stolen as well. Which means we can now expect even more sophisticated malware
Update 29-Oct-2013:
3 million encrypted customer credit card records stolen. At least 38 Million users impacted. More details
Update 10-Nov-2013:
"Operation Hangover" based in India, and used a zero-day Microsoft vulnerability that has been patched now.
"Operation Hangover" based in India, and used a zero-day Microsoft vulnerability that has been patched now.
2013-10-03
Web Penetration Testing with Kali Linux
I was requested by PacktPub to review a book on Penetration Testing (using Kali). The book is now published and available here.
2013-09-28
Google Chat Delivered To Wrong People!!
A big kick to the Big G - For about 2 days, Google chat messages were being delivered to the wrong people, thanks to some bug in their software.
2013-09-20
Google knows YOUR WiFi Password!
Google has access to clear-text wifi passwords. Now considering there are 900 Million+ android devices, and each device would have multiple wifi passwords stored on them - do the maths!
Meaning all the good folks at NSA need to do is but send a request to Google asking for the wifi password of anyone, so that they could snoop in on their computers
Meaning all the good folks at NSA need to do is but send a request to Google asking for the wifi password of anyone, so that they could snoop in on their computers
2013-09-19
2013-09-18
New Bank Hacking Plot
Now we have some guys who try to break into a bank, by installing a supposedly KVM switches, for the employees, but which could transmit keyboard strokes and computer screen! Now, that's new
2013-09-14
Evolution of Hacking
How hacking techniques have (not) evolved in the last 30 years or so. An interesting article.
- Hackers have changed very little since the 1980s (there have always been moral and immoral hackers)
- Hacking technologies have changed very little
- Motivations have changed very little (it has always been for fun or profit)
- Opportunities have changed dramatically
2013-09-04
Social Engineering Attacks
Articles like these remind us that attacks are not always about technical knowledge and finding vulnerabilities. A smart guy, armed with just a phone, can do equally serious damage.
2013-08-27
China under DDoS attacks!
The hunter becomes the prey! China is under attack from undisclosed sources.
2013-08-19
Zmap the fast scanner
2013-08-16
Gmail says users have no right to privacy
This is plain ridiculous.
Google said that "just as a sender of a letter to a business colleague cannot be surprised that the recipient's assistant opens the letter, people who use Web-based e-mail today cannot be surprised if their communications are processed by the recipient's ECS provider in the course of delivery."
2013-08-14
Economics of CyberCrime
Update 03-May-2012:
Update 08-Oct-2012:
As per, "The 2012 Cost of Cyber Crime Report", some highlights:
Microsoft Researchers say cybercrime loss estimates are a bunch of bunk. In "Sex, Lies and Cybercrime Surveys", the Microsoft Researchers wrote, "Cyber-crime, like sexual behavior, defies large-scale direct observation and the estimates we have of it are derived almost exclusively from surveys." The research paper concludes.Pretty Interesting
Update 08-Oct-2012:
As per, "The 2012 Cost of Cyber Crime Report", some highlights:
- The frequency of successful cyber attacks has more than doubled over the last three years
- The annual cost to organizations has slowed dramatically in the last two years
- The average time to resolve a successful attack has grown from 14 days in 2010, through 18 days in 2011, to 24 days in 2012
- Most costly cyber crimes are those caused by malicious insiders, denial of services, and malicious code
2013-08-11
How To Use Tor?
I thought it would be good to read about how to use Tor correctly. It's important to note, that by itself Tor is an extremely good project to protect privacy. It is not perfect, and has some potential loopholes. Usually, the issue lies with the applications users try to run on top of Tor. Intentionally or unintentionally they end up giving away the privacy.
However, till the time there is a 'better' solution made available, let's say this is the best we have!!
0/ Download Tor Browser Bundle, which comes with Tor and a customized Firefox browser
1/ Chrome: Use these instructions to setup Chrome to use Tor. Another method is here
2/ uTorrent: This is not recommended by Tor, but some settings are here
The ideal way to use tor, by setting up a proxy, and a client can only and only connect to it.
Can you break Tor, Russia has $100K as an award for you. Well at least that is publicized, maybe FBI has a bigger one to offer, under the covers.
However, till the time there is a 'better' solution made available, let's say this is the best we have!!
0/ Download Tor Browser Bundle, which comes with Tor and a customized Firefox browser
1/ Chrome: Use these instructions to setup Chrome to use Tor. Another method is here
2/ uTorrent: This is not recommended by Tor, but some settings are here
The ideal way to use tor, by setting up a proxy, and a client can only and only connect to it.
Can you break Tor, Russia has $100K as an award for you. Well at least that is publicized, maybe FBI has a bigger one to offer, under the covers.
PirateBrowser
PirateBay launches PirateBrowser (a customized version of Firefox) to circumvent censorship, and improve anonymity!
2013-08-09
Google Chrome's Password Storage
Stop storing passwords on Chrome. Looks like the passwords are not encrypted with a master password, and hence visible to anyone with physical access to your system.
2013-08-08
FBI vs TOR
FBI's compromising TOR!
This is going to be a story which has created some commotion in the e-world. Major blow to the anonymity and privacy activists in the internet world!!
So, how does it unravel?
1/ FBI arrests the operator of a Tor-based internet host 'Freedom Hosting', for child porn.
2/ They inject some javascript in its webpages, to compromise the identities of the users, by sending user's IP, hostname, MAC address to a server in Virginia, USA. Some technical details.
3/ Similarly TorMail and Tor Browser Bundles are compromised
4/ TorProject.org was quick to announce that they are no way related to Freedom Hosting (which of course is true for any open source, volunteer organization)
5/ It is 'suspected' that FBI also runs numerous TOR nodes, which helps them break its anonymity.
An interesting article by Bruce Schneier around Government, security and privacy.
Also must read - How to use Tor
This is going to be a story which has created some commotion in the e-world. Major blow to the anonymity and privacy activists in the internet world!!
So, how does it unravel?
1/ FBI arrests the operator of a Tor-based internet host 'Freedom Hosting', for child porn.
2/ They inject some javascript in its webpages, to compromise the identities of the users, by sending user's IP, hostname, MAC address to a server in Virginia, USA. Some technical details.
3/ Similarly TorMail and Tor Browser Bundles are compromised
4/ TorProject.org was quick to announce that they are no way related to Freedom Hosting (which of course is true for any open source, volunteer organization)
5/ It is 'suspected' that FBI also runs numerous TOR nodes, which helps them break its anonymity.
An interesting article by Bruce Schneier around Government, security and privacy.
Also must read - How to use Tor
2013-08-05
Stealing Google Authentication
Single sign on is a boom - even for the hackers. A hacker shows how to steal authentication token
2013-08-04
SSL Broken in 30 Seconds
2013-08-03
Windows 8 Secure Boot Bypassed!
Not surprisingly there are security flaws in the Windows 8, around the implementation of Secure Boot by a few vendors.
2013-08-01
2013-07-28
Hacking Cars!
The famous Charlie Miller (on Govt funding) shows how to hack a car. The brakes, the speed, fuel-gauge and everything else! You Tube video here.
Update 01-Aug-2013:
A similar hacker/researcher in UK, has been banned by the court to reveal his findings.
Update 01-Aug-2013:
A similar hacker/researcher in UK, has been banned by the court to reveal his findings.
2013-07-22
Millions of mobile sim cards vulnerable!
Mobile sim cards, which are still on the old technology, with DES encryption are all vulnerable to an attack
2013-07-21
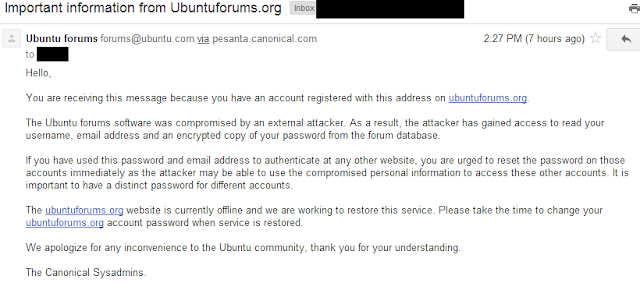
Ubuntu Forums Hacked - 2M Accounts Breached
UbuntuForums has been compromised and led to all the accounts credentials being stolen. The site (thankfully) discloses that the passwords were not stored in plain text, but doesn't mention if best-practices like salting were used. Sputn1k has claimed responsibility.
Update 24-Jul-13:
An email received from Ubuntu:
Update 24-Jul-13:
An email received from Ubuntu:
2013-07-17
Tumblr Passwords Compromised
Tublr asks users to change their passwords. Some mobile app of theirs sent passwords in clear text
2013-07-12
Security for the paranoid!
We all have 100s of accounts, with multiple passwords. So, how can we ensure user friendliness of a password manager, but from a truly [paranoid] security guy's point of view?
We are heading into a world of cloud computing where trust is going to be a huge issue. It is no longer simply a matter of trusting that the software you buy works as advertised.
India VS RIM
I thought I had blogged about the Government of India and Blackberry's RIM debate. But, I can't find it now. Basically the government is pressurizing for something that does not exist.
Update: 06-Jan-13
RIM gives in and sets up a monitoring facility for the Govt of India.
Update: 12-Jul-13:
Looks like BB/RIM finally gave in to the demands of the Indian Govt. But, earlier didn't they say they do not have access to the encryption keys, so how does this magic happen now?!
Update: 06-Jan-13
RIM gives in and sets up a monitoring facility for the Govt of India.
Update: 12-Jul-13:
Looks like BB/RIM finally gave in to the demands of the Indian Govt. But, earlier didn't they say they do not have access to the encryption keys, so how does this magic happen now?!
2013-07-09
Thousands of Club Nintendo accounts compromised
Following the footsteps of the Sony PlayStation hack, accounts of thousands of Nintendo users have been compromised.
99% of Android Devices Vulnerable
Impact: Every device sold since Android 1.6 (Donut); that is, nearly 900 million device
Update 17-Jul-13:
A second similar master-key vulnerability has been discovered.
[Quote] The vulnerability is a code signing flaw. Developer's 'sign' their apps with a cryptographic signature. That way, only the app developer is able to update or modify an existing app, because only the developer has the signature. Bluebox has discovered a way to subvert this. "This vulnerability makes it possible to change an application’s code without affecting the cryptographic signature of the applicationBlog from the Bluebox - a new player in the market
Update 17-Jul-13:
A second similar master-key vulnerability has been discovered.
2013-07-08
Data Leakage By Dumb Employees
How do you know, if your users have auto-forward feature enabled on their email systems? Risk here of course being that confidential data of the organization goes out automatically? How do you detect such offenders? It's harder than you would think it would be
2013-07-06
Carberp financial malware gets leaked online
Source code for a malware, which originally costs $5000, is up for grabs. Go ahead and tweak your own free malware!
Update 18-Aug-2013:
Here is a link to download it.
Update 18-Aug-2013:
Here is a link to download it.
A world record attempt at CTF Hacking Contest
An inspirational attempt to get 3000+ security enthusiasts together and play the Capture The Flag hacking game. If successful, they will go down in the Guinness book of world records! Do watch their youtube video
Microsoft announces a bug bounty program
Microsoft, even though late in this game, has finally announced their very own bug bounty program.
More details of how it works, pays at least $500!
More details of how it works, pays at least $500!
Pakistan Goes For Internet Censorship
Looks like Pakistan is on the same route as China, and will start censoring the internet!
2013-06-15
Spying by a common citizen
A funny and interesting story of how much damage to privacy can be done by any ordinary citizen.
2013-06-14
Iranians under phising attacks
Iran. Political motive, just ahead of elections. Result is rise in Gmail phising
2013-06-09
Drupal's 1 M user accounts breached!
Quote: This access was accomplished via third-party software installed on the Drupal.org server infrastructure, and was not the result of a vulnerability within Drupal itself.
Organziation - Data Leakage
Some disturbing statistics on employees using cloud-services to store/review organization's documents.
2013-06-07
NSA data snooping!
Unbelievable how much data these guys are spying on!
Did NSA manage to decrypt BlackBerry data as well? RIM has declined for now.
NSA Director talks about this program (named PRISM)
Was Microsoft providing vulnerabilities to NSA?
An upcoming app, which promises to defeat all these govt snooping. Already raised 100K in 36 hours!
How much does it cost the govt to eavesdrop on people? Substantial amount of money actually!
DNI Presenter a tool used by NSA to capture citizen's personal chats and messages!
FBI engaged hackers to deploy malware on Android phones.
XKeyscore – the Front End that Queries the NSA Databases
Update 10-Aug-2013:
NSA 'nicely' asks lavabit and SilentText to shut down. They were instrumental in providing end-to-end encrypted email services.
Update 17-Sep-2013:
Some open source tools to help non-NSA folks, achieve some similar reconnaissance.
Update 19-Sep-2013:
NSA purchased 0-days from Vupen (French security researchers)
Update 28-Sep-2013:
NSA even spied on Indian Embassy and UN
Update 29-Oct-2013:
Firefox launches "Lightbeem"
Update 10-Nov-2013:
Crowd sourcing project to audit TrueCrypt
Update 12-Nov-2013:
Charges against Snowden to be dropped ?!
Update 13-Nov-2013:
Google outraged over NSA's extent of spying on its data centres
Update 08-Dec-2013:
Tracking all Snowden documents
Update 22-Dec-2013:
NSA bribed [for $10m] RSA for keeping a bacdoor in their products!
Not surprisingly RSA declines it.
Update 18-Jan-2014:
Obama announces some reforms
Update 28-Jan14:
How Angry Birds helped NSA
Update 29-Jan-14:
Snowden nominated for Nobel
Update 22-Mar-14:
Google tightens HTTPS protection.
Update 08-May-14:
A few email exchanges between NSA and Google released. Doesn't say much, unlike the hype
Update 17-Oct-15:
How the NSA broke encryption (DH algo).
Did NSA manage to decrypt BlackBerry data as well? RIM has declined for now.
NSA Director talks about this program (named PRISM)
Was Microsoft providing vulnerabilities to NSA?
An upcoming app, which promises to defeat all these govt snooping. Already raised 100K in 36 hours!
How much does it cost the govt to eavesdrop on people? Substantial amount of money actually!
DNI Presenter a tool used by NSA to capture citizen's personal chats and messages!
FBI engaged hackers to deploy malware on Android phones.
XKeyscore – the Front End that Queries the NSA Databases
Update 10-Aug-2013:
NSA 'nicely' asks lavabit and SilentText to shut down. They were instrumental in providing end-to-end encrypted email services.
Update 17-Sep-2013:
Some open source tools to help non-NSA folks, achieve some similar reconnaissance.
Update 19-Sep-2013:
NSA purchased 0-days from Vupen (French security researchers)
Update 28-Sep-2013:
NSA even spied on Indian Embassy and UN
Update 29-Oct-2013:
Firefox launches "Lightbeem"
Update 10-Nov-2013:
Crowd sourcing project to audit TrueCrypt
Update 12-Nov-2013:
Charges against Snowden to be dropped ?!
Update 13-Nov-2013:
Google outraged over NSA's extent of spying on its data centres
Update 08-Dec-2013:
Tracking all Snowden documents
Update 22-Dec-2013:
NSA bribed [for $10m] RSA for keeping a bacdoor in their products!
Not surprisingly RSA declines it.
Update 18-Jan-2014:
Obama announces some reforms
Update 28-Jan14:
How Angry Birds helped NSA
Update 29-Jan-14:
Snowden nominated for Nobel
Update 22-Mar-14:
Google tightens HTTPS protection.
Update 08-May-14:
A few email exchanges between NSA and Google released. Doesn't say much, unlike the hype
Update 17-Oct-15:
How the NSA broke encryption (DH algo).
How secure are passwords?
Arstechnica plans to bruteforce 16K hashed passwords. A non-techie editor breaks 47% of them. One expert breaks 82% in one hour!!
2013-06-04
2013-06-01
The World of Financial Trojans
A symantec's report on trojans - I am sure it will be super biased by the business of the creator
Major US Weapons Compromised By Chinese Hackers
Quote:
"...[T]he cyber threat is serious and... the United States cannot be confident that our critical Information Technology (IT) systems will work under attack from a sophisticated and well-resourced opponent utilizing cyber capabilities in combination with all their military and intelligence capabilities," the public version of the DSB report said. "This conclusion was developed upon several factors, including the success adversaries have had penetrating our networks..."
Two Factor Auth
More companies finally following Google's footsteps and enabling 2FA. Twitter ; Linkedin
Update 09-Aug-2013:
Twitter's state of the art 2FA app
Update 09-Aug-2013:
Twitter's state of the art 2FA app
2013-05-31
Google gives 7 days to vendors to patch 0-days!
Google gives 7 days to vendors to patch 0-days! Sounds like a tight deadline from Google.
Update 07-Jun-13:
Google increases the bounty for the bugs found on their own systems!
Update 07-Jun-13:
Google increases the bounty for the bugs found on their own systems!
2013-05-28
2013-05-27
Sky news apps defaced!
Update 27-May-2013
Hackers break into Android apps of a Sky News??!!! Looking for some more details here.
Update 28-May-2013
This explains the matter better.
Hackers break into Android apps of a Sky News??!!! Looking for some more details here.
Update 28-May-2013
This explains the matter better.
2013-05-22
Skype (for)gets end-to-end encryption
There used to be a time when a new (but only) player on the web, had the capability of providing end-to-end (peer-to-peer) encryption. Since Microsoft took it over, looks like privacy is going down the drain.
2013-05-20
2013-05-14
Pen Testing Tutorials
PenTesterLab.com: Looks like a place for interesting, hands-on tutorials. Not too many exercises available for now, but got a few good ones like - Linux Server Hardening, Website Vulnerability review, etc.
2013-05-12
What do employees think about security?
- half of sales-focused employees say their job is hindered because they aren’t getting access to all the information they need
- an alarming 46% avoided the possibility of losing a sales opportunity by bypassing security controls to access necessary sensitive information to get the job done
Full Article
2013-05-11
Card Industry's $45M Fraud
We have a new case where the thieves walked away with $45 million!
It's a known fact that the so-called PCI standard is poor and outdated. The question is when will the industry wake up and either create a new baseline standard?
Or maybe this is a good opportunity to fill this gap today and roll out a new standard.
Here's a high level summary of the heist!
It's a known fact that the so-called PCI standard is poor and outdated. The question is when will the industry wake up and either create a new baseline standard?
Or maybe this is a good opportunity to fill this gap today and roll out a new standard.
Here's a high level summary of the heist!
Name.com Breached
A domain registrar breached, and then forces customers to reset their passwords. Such attacks are always critical, and almost out of the hands of the poor owners of the websites.
India's Cyber Policy
India (finally) works on a cyber security policy/framework. Much needed, but I'm still waiting to see the actual document.
Update 17-Sep-13:
A very good article around India's position for IT Sec and the challenges.
Update 17-Sep-13:
A very good article around India's position for IT Sec and the challenges.
2013-05-07
AutoIt Malwares
AutoIt, which is a Windows scrpting language is now popularly being used to create malwares. In fact there is some really good code on Pastebin up for grabs!
OpUSA
Update 07-May:
Anonymous' threat to attack a huge number of American banks today (7th)
Update 13-May:
Looks like the event wasn't a big success. A few low profile hacks is all they got.
Anonymous' threat to attack a huge number of American banks today (7th)
Update 13-May:
Looks like the event wasn't a big success. A few low profile hacks is all they got.
2013-05-02
Elements of a successful security awareness program
The 7 elements to make your organization's program a success.
Google Glass Bug!
Okay, we now have a cutting edge tool, to keep humans always 'connected', making sc-fi cyborgs a reality. Anyway, this Google brainchild is now available to a limited set of developers, and one of them has a detailed analysis of it.
The concerns with this new technology are probably more than the benefits for now. Here's one article on it.
The concerns with this new technology are probably more than the benefits for now. Here's one article on it.
2013-04-25
AP's Twitter account hacked; false 'Obama injured' tweet sent
Associated Press' twitter account gets hijacked. Intruder posts, "two explosions in the White House and Barack Obama is injured". The tweet was only visible for a matter of minutes, but the Dow Jones industrial average took a nose dive.
Anyone still thinks, cyberwar is science fiction?
Update 25-Apr-2013:
Some rocket-science theory (for me) that this news did not have that big an impact. However, this theory still confirms there was some impact.
LulzSec leader charged
P2P File Sharing
A much needed solution, for peer-2-peer secure sharing. I can already think of a hundred ways how this service is going to be misused!
2013-04-21
2013-04-20
Home routers contain critical security vulnerabilities
Popular products like the following vulnerable:
Linksys WRT310v2, Netgear's WNDR4700, TP-Link's WR1043N, Verizon's FiOS Actiontec MI424WR-GEN3I, D-Link's DIR865L and Belkin's N300, N900 and F5D8236-4 v2 models
Different Types of CISO's
A good sum-up of the three types of CISO's:
- The non-techie, but business-savvy CISO
- The technically competent, but less business-articulate CISO
- The hybrid CISO
2013-04-13
Bitcoinica, twice hacked in 2012, is being sued
Update 29-Aug-2012:
This may well be the beginning of the end for Bitcoinica..!
Update 05-Sep-2012:
Update 26-Sep-2012:
Back Online
Update 04-Apr-2013:
Bitcoin under attack again, a DDoS and a DB hack.
Update 13-Apr-2013:
Some explanation around the economics of bitcoin. Seems like the currency has been super volatile recently.
This may well be the beginning of the end for Bitcoinica..!
Update 05-Sep-2012:
Hackers stole about US$250,000 from BitFloor, a BitCoin exchange, on Monday, and it does not have the money to reimburse account holders, according to the website's founder.More technical details here
Update 26-Sep-2012:
Back Online
Update 04-Apr-2013:
Bitcoin under attack again, a DDoS and a DB hack.
Update 13-Apr-2013:
Some explanation around the economics of bitcoin. Seems like the currency has been super volatile recently.
Programmable HID USB Keystroke Dongle
Programmable HID USB Keystroke Dongle
Update 13-Apr-13:
Integrating it with Kali - A super easy tutorial for a powerful tool.
AKA : Rubber Duck
AKA: PHUKD
AKA: Teensy
Multiple names, to something small, but an extremely powerful attack:
It's a neat little USB dongle which looks like a thumbdrive that you could surreptitiously install in the back of someone's computer. The Phantom Keystroker acts as a keyboard/mouse USB HID (Human Interface Device) to send keystrokes, move the mouse pointer around randomly, toggle caps lock and other things to annoy your co-workers and loved ones.Read what IronGeek has to say, Hak5's version (available under $20 now).
Update 13-Apr-13:
Integrating it with Kali - A super easy tutorial for a powerful tool.
2013-04-07
Malware Deep Dive
InfoWorld's report on malware analysis. As always some scary statistics - the accuracy of which is always doubtful, and biased coming from antivirus companies.
However, there is a good list of pointers for the newbies to stay safe from viruses.
Report is here
However, there is a good list of pointers for the newbies to stay safe from viruses.
Report is here
2013-03-29
Role of Auditors
Being in a financial organization, makes audits, integrated in the DNA of every IT professional. The audits varies from internal, external, regulatory, statutory, to what not. So, are these of any value?
Personally, I have a lot of respect for the audit function. Especially the IT Security audit. However, I prefer working with auditors who know their jobs, and try and look for real risk, and are not just mechanical bots trained to match documents to their check-lists.
Here is one article that is in-sync to my thoughts.
Personally, I have a lot of respect for the audit function. Especially the IT Security audit. However, I prefer working with auditors who know their jobs, and try and look for real risk, and are not just mechanical bots trained to match documents to their check-lists.
Here is one article that is in-sync to my thoughts.
Spamhaus' website hit by a 300Gbps DDoS
2013-03-06
2013-03-05
Evernote hacked! Change Password Now
50 million + users impacted.
An interesting article - Should websites be required to publicly disclose their password storage strategy?
Following hack, Evernote speeds move to two-factor authentication
An interesting article - Should websites be required to publicly disclose their password storage strategy?
Following hack, Evernote speeds move to two-factor authentication
2013-03-01
Bank of America Loses Confidential (?) Data
BOA had some 14 GB of data stored on a public server, which was misconfigured, and anyone could log on to it. With salary details, source code, and what not.
2013-02-28
ABC News Hacked
ABC News hacked, for some controversial interview. The hacker publishes the full DB dump, including password hashes. Findings:
In short - nothing new.
- No salting
- Weak password used by users.
In short - nothing new.
2013-02-27
Good News - Burger King's Twitter Account Hijacked
Burger King's Twitter account get hijacked, and the imposter jokes, saying McDonald's is taking over Burger King.
Anyway, BK is all smiles, this little episode more than doubled its followers..! No publicity is bad publicity.
2013-02-25
Email Spoofing
So, I was looking for some good tools to spoof emails. To know what is "email spoofing", please refer to Wikipedia. I tried some popular websites, like:
Update: 25-Feb-13
A very good video tutorial to clone a website, and send out spam, using Backtrack's SET
http://emkei.cz/Both most likely the emails sent from here gets tagged as spam. Recommended is using tools like (built into Bactrack) SET and SendEmail. Challenge of course is finding a good & reliable SMTP server. In the screenshot below, used Gmail's server:
http://www.sendanonymousemail.net/
Update: 25-Feb-13
A very good video tutorial to clone a website, and send out spam, using Backtrack's SET
2013-02-20
New York Times Hacked by China
Looks like Symantec became overly defensive here.
Update 20-Feb-2012:
NY times, engages Mandiant (a security firm), who releases a report, that says majority of the hacks in China are state sponsored!! And of course the Govt of China refutes. Full report is here.
Update 22-May-2013:
Attacks are back with a slight modification.
Update 20-Feb-2012:
NY times, engages Mandiant (a security firm), who releases a report, that says majority of the hacks in China are state sponsored!! And of course the Govt of China refutes. Full report is here.
Update 22-May-2013:
Attacks are back with a slight modification.
2013-02-12
Megaupload Shut Down
20-Jan-2012:
Megaupload, a file sharing website has been closed down, and arrested it's founder in a very dramatic style.
23-Jan-12:
Mr. Dotcom (AKA Kim Schmitz) has recruited Robert Bennett (known for defending President Bill Clinton during the Lewinsky scandal).
Not surprisingly, Anonymous started a retaliation attack, hours after the arrest was announced. However, this time their accomplices in the attack were unsuspecting internet users.
22-Feb-2012:
Kim is granted bail, with a long list of conditions
01-Mar-2012:
A TV interview with Kim Dotcom
05-Mar-2012:
Hackers fool Anonymous and their supporters.
Not surprisingly Anonymous refutes the claim that there was malware in their DDoS tool.
19-Mar-2012:
Google defends Hotfile and Megaupload (indirectly). Of course, goes without saying, the real reason here is Google's own Youtube.
01-June-2012:
Another update on this battle. Looks like the lawyers are playing their game now.
21-Jul-2012:
This is insane, Mr KimDotCom releases a video against the president of the USA
22-Jan-2013:
All right people, we now have the new and improved version of megaupload, with a user-side fit-for-army encryption.
24-Jan-2013:
Looks like there are some serious security lapses in this new 'security conscience' website. There is a MegaCracker as well to decrypt passwords from the auto-emails sent to the users.
12-Feb-2013:
Mega calls all white hats
Megaupload, a file sharing website has been closed down, and arrested it's founder in a very dramatic style.
23-Jan-12:
Mr. Dotcom (AKA Kim Schmitz) has recruited Robert Bennett (known for defending President Bill Clinton during the Lewinsky scandal).
Not surprisingly, Anonymous started a retaliation attack, hours after the arrest was announced. However, this time their accomplices in the attack were unsuspecting internet users.
22-Feb-2012:
Kim is granted bail, with a long list of conditions
01-Mar-2012:
A TV interview with Kim Dotcom
05-Mar-2012:
Hackers fool Anonymous and their supporters.
Hackers have duped supporters of the Anonymous group into installing the Zeus botnet, which steals confidential information from PCs, including banking usernames and passwords, security researchers said last week.07-Mar-2012:
Not surprisingly Anonymous refutes the claim that there was malware in their DDoS tool.
19-Mar-2012:
Google defends Hotfile and Megaupload (indirectly). Of course, goes without saying, the real reason here is Google's own Youtube.
01-June-2012:
Another update on this battle. Looks like the lawyers are playing their game now.
21-Jul-2012:
This is insane, Mr KimDotCom releases a video against the president of the USA
22-Jan-2013:
All right people, we now have the new and improved version of megaupload, with a user-side fit-for-army encryption.
24-Jan-2013:
Looks like there are some serious security lapses in this new 'security conscience' website. There is a MegaCracker as well to decrypt passwords from the auto-emails sent to the users.
12-Feb-2013:
Mega calls all white hats
2013-02-11
Operation Last Resort
A new attack by Anonymous, apparently to vengeance the death of Aaron Swartz
Update 11-Feb-13:
Now they attack MIT, but briefly.
Update 11-Feb-13:
Now they attack MIT, but briefly.
Outlook vs Gmail
This is way under the belt..! Microsoft says Google reads all your email (to push ads).
I am not advocating Google, nor do I believe they have the best privacy policy. However, question for Microsoft, if you don't scan emails, how do you filter out spam?
I am not advocating Google, nor do I believe they have the best privacy policy. However, question for Microsoft, if you don't scan emails, how do you filter out spam?
2013-02-07
2013-01-31
Banks Under Cyber Attack
Operation Ababil
Project Blitzkrieg
Update: 26-Sep-2012:
Looks like a number of banks are under cyber attacks. The reason of the attack (as if hackers need a reason), varies from a controversial Youtube video to Iraq wars, etc.
Wells Fargo
JP Morgan, Citi Bank
BNL
Update: 08-Oct-2012:
Banks, especially EU, are gearing up for such attacks. "Cyber Europe 2012" exercise.
Update 09-Oct-2012:
Risk rating went up, as companies gear up for attacks.
Update 20-Oct-2012:
HSBC DDoSed for about one day! For this attack Mrt. Izz ad-Din al-Qassam Cyber Fighters take credit on their pastebin page.
Update 22-Oct-2012:
Looks like we have too many parties taking credit for the HSBC attack
Update 31-Jan-2013:
Now the attack has been called off.
Project Blitzkrieg
Update: 26-Sep-2012:
Looks like a number of banks are under cyber attacks. The reason of the attack (as if hackers need a reason), varies from a controversial Youtube video to Iraq wars, etc.
Wells Fargo
JP Morgan, Citi Bank
BNL
Update: 08-Oct-2012:
Banks, especially EU, are gearing up for such attacks. "Cyber Europe 2012" exercise.
Update 09-Oct-2012:
Risk rating went up, as companies gear up for attacks.
Update 20-Oct-2012:
HSBC DDoSed for about one day! For this attack Mrt. Izz ad-Din al-Qassam Cyber Fighters take credit on their pastebin page.
Update 22-Oct-2012:
Looks like we have too many parties taking credit for the HSBC attack
Update 31-Jan-2013:
Now the attack has been called off.
2013-01-29
LOIC & DDoS
A very good article to explain the technical and legal implications of DDoS, using such tools (as LOIC).
2013-01-24
2013-01-19
Encrypt (almost) anything
A good cheat-sheet article around how to encrypt the usual day-to-day data (emails, USB, hard disks, etc.)
Pwn2Own 2013
All right get set for the most interesting 'capture the flag' battle. This time there is a record $560K on the line, and Google is supportive and one of the funders. This is mostly because, they have flipped back to the previous rules, and not using 2012's rules
Update 29-Jan-2013:
Google stakes Pwnium hacking contest to $3.14M in potential prizes
Update 14-Sep-2013:
Second annual event scheduled in Tokyo, in Nov 2013
Update 14-Nov-2013:
Pinkie Pie breaks Samsung S4 and Chrome!
Update 29-Jan-2013:
Google stakes Pwnium hacking contest to $3.14M in potential prizes
Update 14-Sep-2013:
Second annual event scheduled in Tokyo, in Nov 2013
Update 14-Nov-2013:
Pinkie Pie breaks Samsung S4 and Chrome!
Nokia's MITM on HTTPS Traffic
A security researcher discovered that Nokia was intercepting encrypted traffic, and decrypting it. Which of course is a major security concern. Nokia has admitted that they do decrypt, but only to improve the performance.
Makes you wonder what is the "right" balance between security and performance? Schneier thinks Nokia's action may become the industry norm.
Makes you wonder what is the "right" balance between security and performance? Schneier thinks Nokia's action may become the industry norm.
2013-01-15
Another Critical Java Vulnerability
A few days ago, another critical 0-day vulnerability was released on Java.
Troy has an interesting article, if it is possible to survive without Java today - he believes it is possible.
Troy has an interesting article, if it is possible to survive without Java today - he believes it is possible.
2013-01-12
Make DDoS legal!
Anonymous requests President Obama to make DDoS legal. However, doesn't look like their petition is doing too well.
2013-01-09
2013-01-04
Fake Google's Certs
The certificate was erroneously issued by an intermediate certificate authority (CA) linking back to TurkTrust, a Turkish CA.Full Story Here.
How it could have been detected by Google.
2013-01-02
PGP, TrueCrypt-encrypted files CRACKED by £300 tool
Forensic Disk Decryptor attempts to unlock information stored in disks and volumes encrypted by BitLocker, PGP or TrueCrypt.Full Story
Cuckoo Sand Box - Analyse Malware
Malware? Tear it apart, discover its ins and outs and collect actionable threat data. Cuckoo is the leading open source automated malware analysis system.CuckooSandBox
Subscribe to:
Comments (Atom)